As APIs become increasingly essential to business operations, the need for observability and security to combat intentional misuse has never been higher. API abuse isn’t just a technical glitch; it’s a severe threat that can lead to data breaches, downtime, and significant reputation loss.
In this article, we’ll delve into API abuse, why it matters, and the proactive steps you can take to protect your business.
What is API Abuse?
Defining API Abuse vs. API Misuse
API abuse occurs when an API is intentionally misused or exploited to perform actions that compromise security, stability, or data integrity. It’s different from API misuse, which generally involves accidental mistakes or incorrect calls by developers. On the other hand, API abuse is deliberate, often conducted by malicious actors seeking unauthorized access to data or services.
To put it more simply:
- API Abuse is the intentional misuse or exploitation of an API. It occurs when attackers deliberately perform actions compromising security, stability, or data integrity.
- API Misuse is the accidental mistakes or incorrect API calls by developers. It occurs when APIs are used improperly, often due to a lack of understanding or errors in implementation.
The Role of API Observability in Detecting Abuse
Real-time observability enables companies to monitor API usage patterns and detect anomalies indicative of abuse. By continuously tracking API behaviors, businesses can gain insights into potential threats before they cause harm.
Why API Abuse is a Major Concern
The risk of API abuse has surged with the shift towards an API-first approach across industries. Factors such as increased third-party integrations and the widespread adoption of microservices architectures have created more access points for exploitation.
This can lead to several consequences, such as:
- Financial Losses: Data breaches and unauthorized API calls can result in lost revenue, fraud-related costs, and unexpected downtime, impacting short- and long-term profitability.
- Operational Impact: High-traffic abuse, such as denial-of-service attacks, can overwhelm systems, affecting functionality and leading to service disruptions.
- Reputational Damage: Security lapses can damage customer and partner relationships, leading to lost business and diminished brand reputation.
Types of API Abuse
Data Scraping
This involves automated bots accessing APIs to extract sensitive or proprietary data. For example, a bot may continuously query a financial data API to collect proprietary pricing information, which can be sold to competitors or misused.
Account Takeovers (ATO)
Malicious actors use credential stuffing or brute-force attacks to gain unauthorized access to user accounts. When successful, ATOs can expose personal data and even lead to fraud.
Denial of Service (DoS) Attacks
Attackers flood an API with many requests, slowing down or crashing services. This can disrupt essential functions and frustrate legitimate users.
API Key Leakage
If API keys are not securely managed, they may be exposed, leading to unauthorized access. Once a key is compromised, attackers can freely access data or services associated with the API.
Real-World Examples of API Abuse
Here are the two most popular API abuse examples of 2024:
Optus API Breach
In this incident, attackers exploited a vulnerability in the Optus API, leading to a data breach that exposed sensitive customer data. This breach led to financial losses and prompted regulatory scrutiny, affecting the company’s long-term credibility.
T-Mobile API Breach
T-Mobile’s API was subject to unauthorized access, exposing data for over 37 million users. T-Mobile’s breach exemplified how a single API vulnerability could result in extensive data loss and erode customer trust.
These cases emphasize the importance of continuous API observability to detect unusual patterns and prevent significant losses. Treblle’s observability feature and anomaly detection capabilities could have helped identify these risks early, potentially preventing abuse before the damage occurred.
How to Prevent API Abuse
While there is no sure-shot way to prevent API abuse, here are some best practices in your API program to prevent them from potential abuse:
Rate limiting and quotas
Limiting the number of requests per user or IP can protect your APIs from abuse tactics like scraping and denial-of-service attacks. Restricting requests can also prevent bots from overwhelming your system and gathering data.
Authentication and authorization
Ensuring secure access is vital. Use API keys, OAuth, and token-based systems to manage authorization securely. Token-based systems with short expiration times can reduce the window for unauthorized access.
Anomaly detection through observability
Observability platforms allow businesses to detect unusual patterns in API requests, such as an IP address suddenly making thousands of requests quickly. This can serve as an early warning sign, enabling quick responses.
Log everything
Comprehensive logging provides a trail of API interactions, essential for spotting suspicious activity. Tools like Treblle offer in-depth insights into API usage, helping teams identify anomalies before they escalate.
How Treblle’s API intelligence platform helps combat API abuse
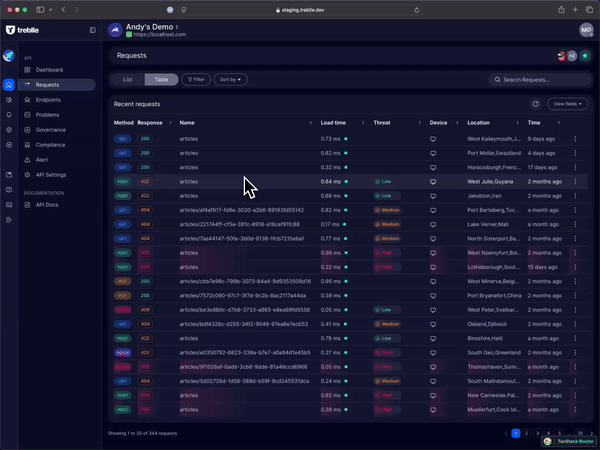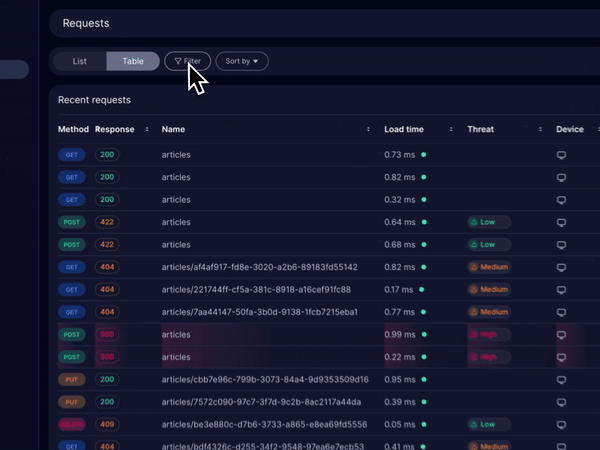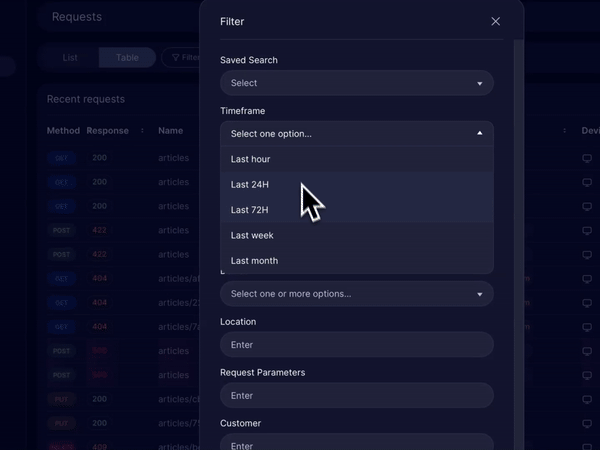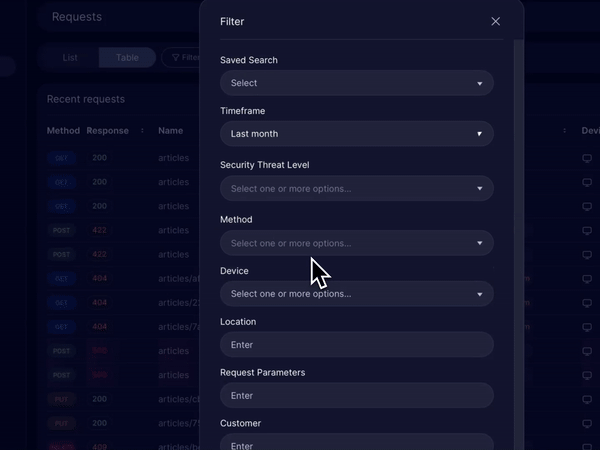
Real-Time Observability
Treblle’s observability feature offers complete visibility into your API’s performance, tracking every request, response, and error as they happen. We provide over 40 API-specific data points per request, helping your team spot unusual patterns like traffic spikes or frequent failures that could signal potential abuse.
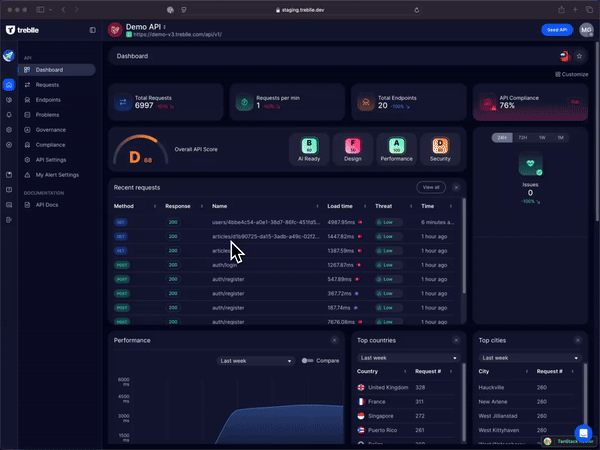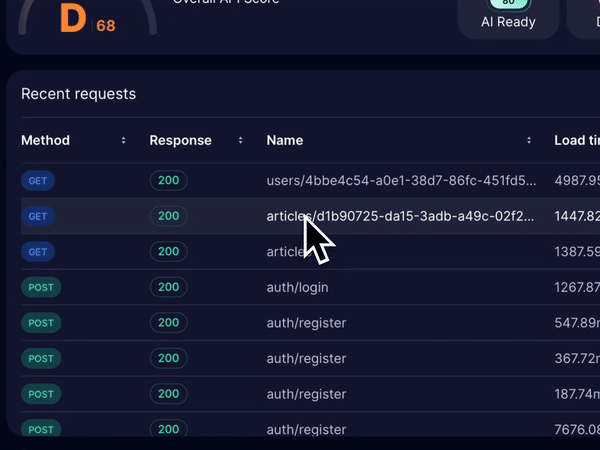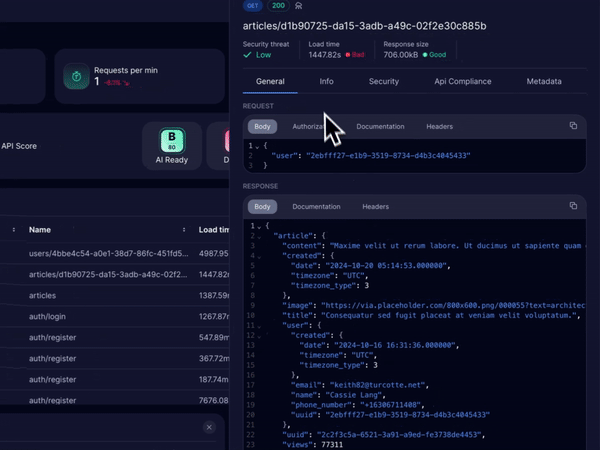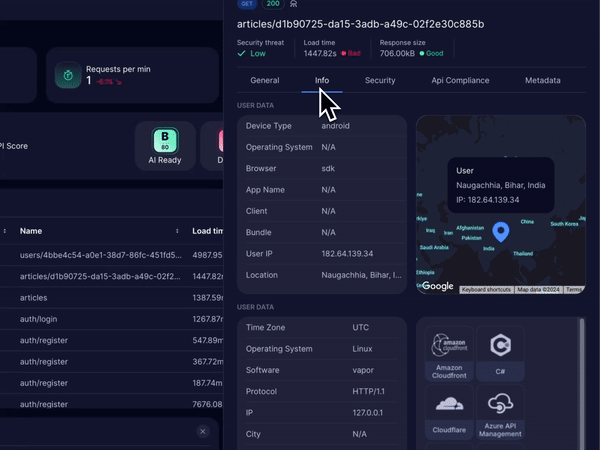
These data points not only help in preventing API abuse, but they also play a significant role in improving the overall security and performance of the APIs.
API Governance
Treblle platform scans each of your API requests for performance, security, and design best practices and scores them against the industry benchmarks while highlighting the areas of improvement against each category.

Advanced Alerting
Treblle allows teams to monitor for abuse patterns with custom alerts. For example, a sudden spike in requests can trigger alerts, giving security teams time to investigate before further damage is done.
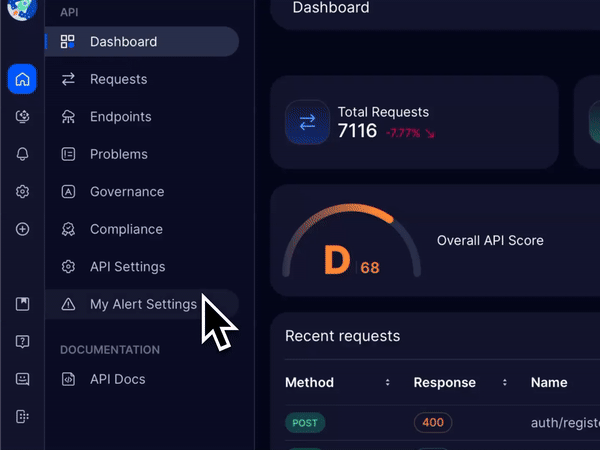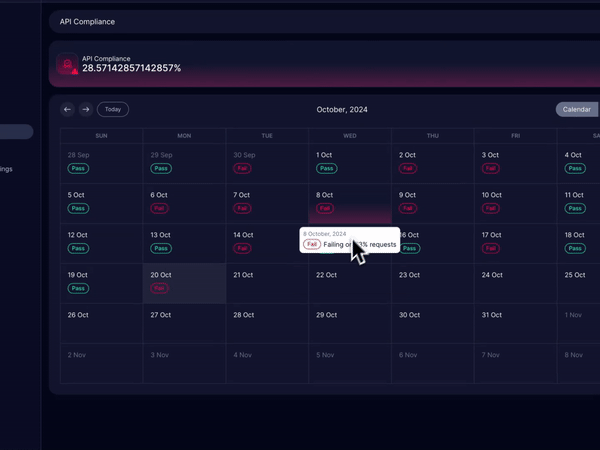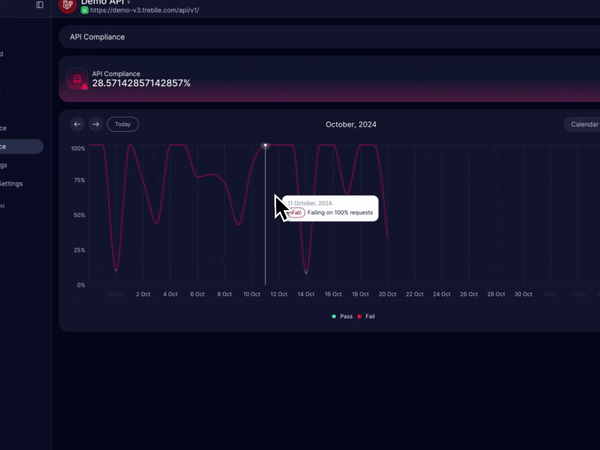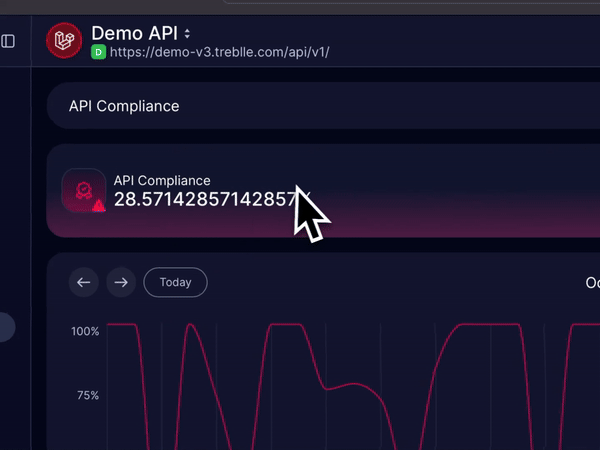
Compliance
Treblle automatically checks all your API requests for GDPR, CCPA, and PCI-compliant and updates you if the API request fails to comply, so you can act on them before it’s too late.
Collaboration and Workspaces
Treblle’s workspaces allow cross-functional teams to collaborate on API observability. For example, if one team spots a pattern indicative of abuse, they can quickly communicate findings and coordinate a response with other stakeholders.

Key takeaways for protecting APIs from abuse
The evolving threat of API abuse means businesses must adopt an ongoing, proactive approach to API security. Here’s what’s essential:
- Prioritize Real-Time Observability: Observing your API traffic is critical for detecting abuse patterns and ensuring a rapid response.
- Implement Layered Security Tactics: Combine rate limiting, secure authentication, and anomaly detection for a robust defense strategy.
- Use Comprehensive Tools: Platforms like Treblle bring together observability, anomaly detection, and privacy features, along with team collaboration capabilities, in one place, making it easier to safeguard APIs from potential threats.
Conclusion
API abuse is a serious risk to businesses that rely on APIs for critical services and data access. As API abuse tactics become more sophisticated, protecting APIs requires robust observability, multi-layered security, and proactive threat detection.
Treblle’s API intelligence platform provides the real-time observability, advanced alerting, and privacy tools necessary to guard against abuse. By implementing these strategies and tools, businesses can maintain control over their APIs and ensure a safe, secure digital environment for their users.






