API security.
Last year breaches involving big names like T-Mobile and Honda have thrown this topic into sharp focus, and rightfully so.
Insecure APIs can expose sensitive customer data, leading to a nightmare of identity theft, phishing attacks, and reputational damage for your company.
Last year, we wrote that API Security is a top concern for businesses and organizations.
It seems like that behind the scenes there lies a dark and overlooked aspect of API Security.

T-Mobile Data Breaches
T-Mobile disclosed two data breaches in 2023, affecting millions of customers. The first breach, disclosed on January 19, 2023, impacted 37 million customers, while the second breach, disclosed on June 23, 2023, affected 836 customers.
Nature of Breaches
- The attacker exploited a vulnerability in an API to steal the personal information of customers, including names, phone numbers, email addresses, and account PINs.
- The second breach involved the exploitation of a vulnerability in T-Mobile's website to gain access to the personal information of customers.
Impact
- Both breaches exposed affected customers to the risk of identity theft and phishing attacks.
- T-Mobile offered affected customers two years of free credit monitoring and identity theft protection.
Prior Incidents
- T-Mobile also experienced email server hacks in 2020 and unauthorized access to customer proprietary network information in 2021.
Honda API Flaws Security Incident
Security researcher Eaton Zveare discovered two vulnerabilities in Honda's e-commerce platform for power equipment, marine, lawn & garden, which allowed unauthorized access to customer data and admin panels.
Vulnerabilities
- The discovered vulnerabilities enabled anyone to reset the passwords of any account on the platform and access the admin panels of all Honda dealers.
- The vulnerabilities were caused by a lack of access controls on the platform, allowing unauthorized access to sensitive data.
Data Exposure
- The password reset vulnerabilities could have exposed customer data such as names, addresses, email addresses, and phone numbers.
- The admin panel vulnerabilities could have exposed even more sensitive data, such as dealer sales figures, inventory levels, and customer purchase history.
Response
- The vulnerabilities were discovered in January 2023 but were not disclosed until June 2023, indicating a delayed response to the security issues.
Importance of Security
- The incident serves as a reminder of the importance of security for businesses and the need to carefully review security practices to protect customer data.
These incidents highlight the critical need for robust API security measures, proactive adoption of best practices, and timely response to security vulnerabilities to protect customer data and maintain a safe and trusted environment.
Why API Security Matters More Than Ever
The incidents involving T-Mobile and Honda underscore the critical importance of API security. Businesses and developers must prioritize the security of their APIs to safeguard sensitive customer data. To delve deeper into the intricacies of API security, our article on the untold secrets of API security goes into detailed exploration.

Insecure APIs pose significant risks, including data breaches, financial loss, reputational damage, and legal implications, highlighting the urgent need for robust API security measures.
Here's why you should prioritize API security:
- Comprehensive API Inventory and Documentation: Identify and
document every APIin your ecosystem to gain a thorough understanding of the API landscape. - Strong Authentication and Authorization: Ensure that APIs require proper credentials, such as
tokensandcertificates, for access, thereby mitigating unauthorized access and potential breaches. - User Input Validation: Implement robust user input validation to sanitize data and prevent
injection attacksand other vulnerabilities, enhancing the overall security posture of your APIs. - Encryption of API Traffic: Protect data in transit between clients and servers by employing
HTTPSto encrypt allAPI traffic, safeguarding sensitive information from unauthorized access. - Regular Vulnerability Testing and Scanning: Conduct
regular penetration testingandsecurity auditsto identify and address weaknesses in APIs, thereby ensuring proactive mitigation of potential vulnerabilities. - Continuous Monitoring for Suspicious Activity: Implement robust
monitoringof API activity to track access patterns and detect anomalies that might indicate potential breaches, allowing for timely intervention and response to security threats.
Best Practices for API Security
To improve API security, businesses and developers should implement robust security measures such as API authentication, encryption, and access control.These measures help prevent unauthorized access and protect sensitive data from potential breaches.
Here are some key practices to fortify your API security:
Customer Trust
Customer data is a valuable asset, and breaches due to insecure APIs can severely impact trust. A breach shakes that trust, potentially leading to customer churn and long-term damage to the business's reputation.
Compliance Risks
Data privacy regulations such as GDPR and CCPA carry substantial legal and financial consequences. Breaches resulting from insecure APIs can lead to hefty fines and reputational damage, making compliance a crucial aspect of API security.
Vulnerability to Attacks
Insecure APIs are a prime target for attackers, posing a significant risk of exposing vast amounts of customer data, as evidenced by the breaches at T-Mobile and Honda.
Treblle API Security: An In-Depth Look
Treblle's API security solution provides a comprehensive shield for your APIs, safeguarding them from a wide range of threats.
-> Treblle's API Security!

Fortify Your APIs Today
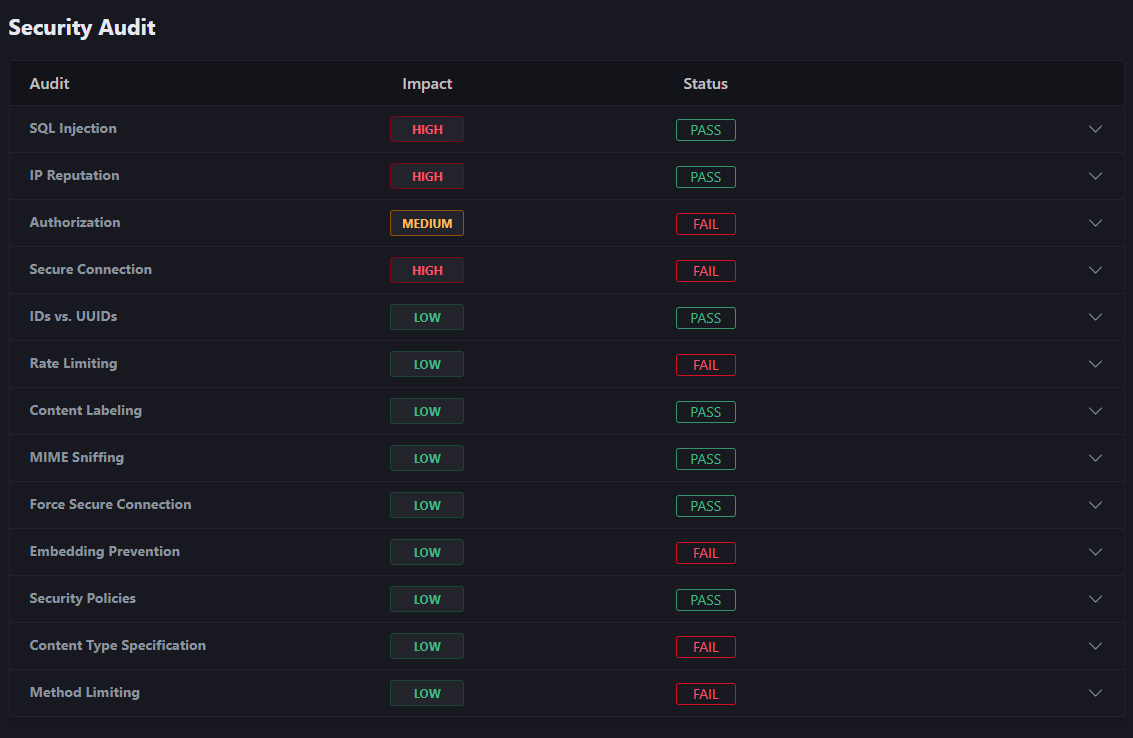
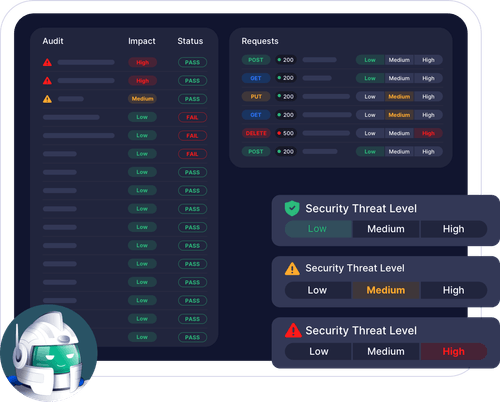
Keep your APIs safe with automated API Security. Treblle makes 15 security checks on every single API request and gives it one of three threat levels: Low, Medium or High.
Automated Security Checks
- These checks identify
vulnerabilitiesand categorize the request's threat level aslow, medium, or high.- SQL Injection: Treblle analyzes the payload sent with every API and detects the most common
SQL injectionpatterns. - IP Reputation: Treblle uses its
own network as well as 3rd partyservices to check the reputation of your user's IP address. - Authorization: Treblle can
automatically detectall forms of authorization on every API request and check to make sure it's being used properly. - Secure Connection (SSL/TLS): Treblle
automatically detectswhether or not the requests your end customers are making are using HTTPs instead of HTTP. - IDs vs. UUIDs: By examining the request URL, Treblle can automatically detect whether or not you're using IDs on your endpoints.
- Rate Limiting: Treblle looks for the
x-rate limit-*headers in the response payload to see if you correctly use rate limiting. - Content Labeling: Treblle checks to see if the
Content-Typeheader exists and if its value is set toapplication/json. - MIME Sniffing: Treblle checks to see if the
X-Content-Type-Optionsheader exists and if its value is set tonosniff. - Force Secure Connection: Treblle looks for the
strict-transport-securityheader in your API responses. - Embedding Prevention: Treblle checks to see if the
X-Frame-Optionsheader exists and its value is set todeny. - Security Policies: Treblle checks to see if the response headers for your requests have a
Content-Security-Policyheader defined. - Content Type Specification: Treblle checks the headers of your request to see if the
Acceptheader exists and if its value is set toapplication/json. - Method Limiting: Treblle checks the headers of your responses to see if the
Allowheader exists.
- SQL Injection: Treblle analyzes the payload sent with every API and detects the most common
Core 15 Checks: Treblle automatically analyzes every single API request against 15 critical security checks.
Enhanced Threat Detection and Response
- Real-time Threat Alerts: Treblle provides instant notifications whenever a security threat is identified in an API request. This allows for immediate investigation and mitigation actions.
- Data Protection & Validation: Treblle ensures that all incoming data is rigorously validated and sanitized. This prevents malicious code injection attempts like SQL injection and improves overall API response time.
API Traffic Spike Analysis: Treblle can evaluate the threat potential of sudden increases in API traffic volume. This helps identify potential denial-of-service attacks or other suspicious activity.

Strengthen Your API Security Now
Safeguard your APIs effortlessly. Treblle conducts 15 security evaluations on every API request, categorizing them into low, medium, or high threat levels for comprehensive protection.
Zero-Trust Security Model
- Comprehensive Threat Assessment: Treblle adopts a zero-trust approach, treating every request with suspicion. This means every request goes through thorough security checks regardless of its origin.
- Encrypted Connections (SSL/TLS): Treblle ensures that all communication between clients and servers is encrypted using HTTPS, protecting data confidentiality and integrity.
- IP Reputation Checks: Treblle automatically checks the reputation of the IP address making the API request, flagging requests from known malicious sources.
Use Cases: How Treblle Safeguards Your APIs Across Industries
Treblle's API security solution caters to a wide range of industries and use cases:
- Financial Services: Protect user financial data and ensure compliance with industry regulations.
- Healthcare: Safeguard sensitive patient information and comply with HIPAA regulations.
- E-commerce: Secure customer data and prevent fraudulent transactions.
- Social Media: Protect user privacy and prevent the spread of misinformation.
- IoT: Secure communication between devices and prevent unauthorized access.
Check this video to learn how you can use Treblle's API Security Feature!
By leveraging Treblle's automated security checks, real-time threat detection, and zero-trust approach, organizations across all sectors can significantly strengthen their API security posture and prevent data breaches like those experienced by T-Mobile and Honda.






